¶ VPN Service
¶ What cryptocurrencies do you accept?
Monero, Bitcoin Lightning, Bitcoin, and Litecoin. If you need Monero, then free speech advocates have discussed OpenMonero.
¶ Do you accept fiat money?
Not directly because this requires bank accounts, which forces the organization to comply with gagged data requests. However, for an order over $50 we can accept a gift card, which we'll resell on the secondary markets.
¶ What data is collected about me?
We do not log use. The only thing saved on our servers is your subscription code, when it ends, and the WireGuard public key or Proxy credentials.
¶ What is the cost?
$1 per location. The current website makes this very fast to get them, with QR codes for the Wireguard config as well. And you can get up to a year if this is a bother.
¶ What are the rules?
We do not allow Denial of Service (DoS) attacks. If we get a DDoS complaint, we will find the subscription(s) participating in the attack, and cancel them. We HAVE to do this to prevent Cloudflare from blocking our IPs.
Also please follow the laws of the country your subscription is in.
¶ Do you allow torrents?
Yes there are no restrictions.
¶ What your policy on erasing WireGuard logs?
After 5 minutes of no connection, we remove and then re-add your WireGuard key, to erase the connection to your IP address. All WireGuard providers deal with this, and most use similar methods.
¶ Can I change WireGuard keys?
Yes of course. For HyraVeil, each profile has it's own key-pair, so you're getting far more diversity from our system, than single key providers. Second, you can delete the wg.config file in .local/hydra-veil for that profile. And then it will connect you to the billing server to get a new public key tied to your subscription.
For the web client on other platforms, if you enter you subscription, it will allow you to generate another key. Keep in mind this is only the key used to verify the session, and does not decrypt the actual Wireguard sessions.
¶ Do you allow Port Forwarding?
No, we do not support port forwarding, due to the potential for abuse.
¶ Can I re-use the same subscription?
Yes, but not at the same time, and all the other profiles would have to be the same location. For WireGuard, the billing server is coordinating giving you a new WireGuard config file each time. This is the downside to reusing subscriptions, slower speed and a little less metadata privacy with the billing server. (Billing server is a different country than your actual subscription country)
¶ What Platforms are supported?
Our browser fingerprint client HydraVeil is only available for Linux. However, you can use our VPN with any WireGuard application. This could include Android, iPhone, Windows, or Apple. Please see our VPN website
¶ What apps do you have?
We currently have a Linux app called HydraVeil focused on browser fingerprint profiles, please see HydraVeil.net. For other platforms, we'll direct you to fast and easy-to-use open source apps, such as WGTunnel on F-droid. These offer quite a number of features that work just as effectively in many situations. In fact, they are usually easier and faster to use than many VPN companies' original apps.

¶ Can I use this VPN on Android, iPhone, Windows, Mac, or a Router?
Yes, Simplified Privacy is:
-far cheaper ($1/month)
-more private server choices than other providers
-isolate your phone from your PC with different billing codes
-be anonymous to anyone, such as another provider on your router.
Please see our tutorial here: link
¶ HydraVeil
¶ Do you save my browser choice?
No, the profile's browser choice, name, and screen size are saved locally on your device. You can download all the browsers at once, and then use them as you please. We don't know or save browser choices tied to subscriptions.
¶ Can I open the profile browser WITHOUT your VPN?
The browser is hardwired to force the traffic through either WireGuard or a Proxy connection. Because it's networking files are isolated, it can't get the internet without the "proxy" connection, which could be WireGuard or Socks5 Proxy.
However, since it's open source, we can't force you to use our service. You could in theory, swap one of our apathetic commodity competitors' WireGuard configurations in the same folder. But keep in mind that our pricing is designed to be lower, to keep your different activities isolated. And you support development of the client and network further.
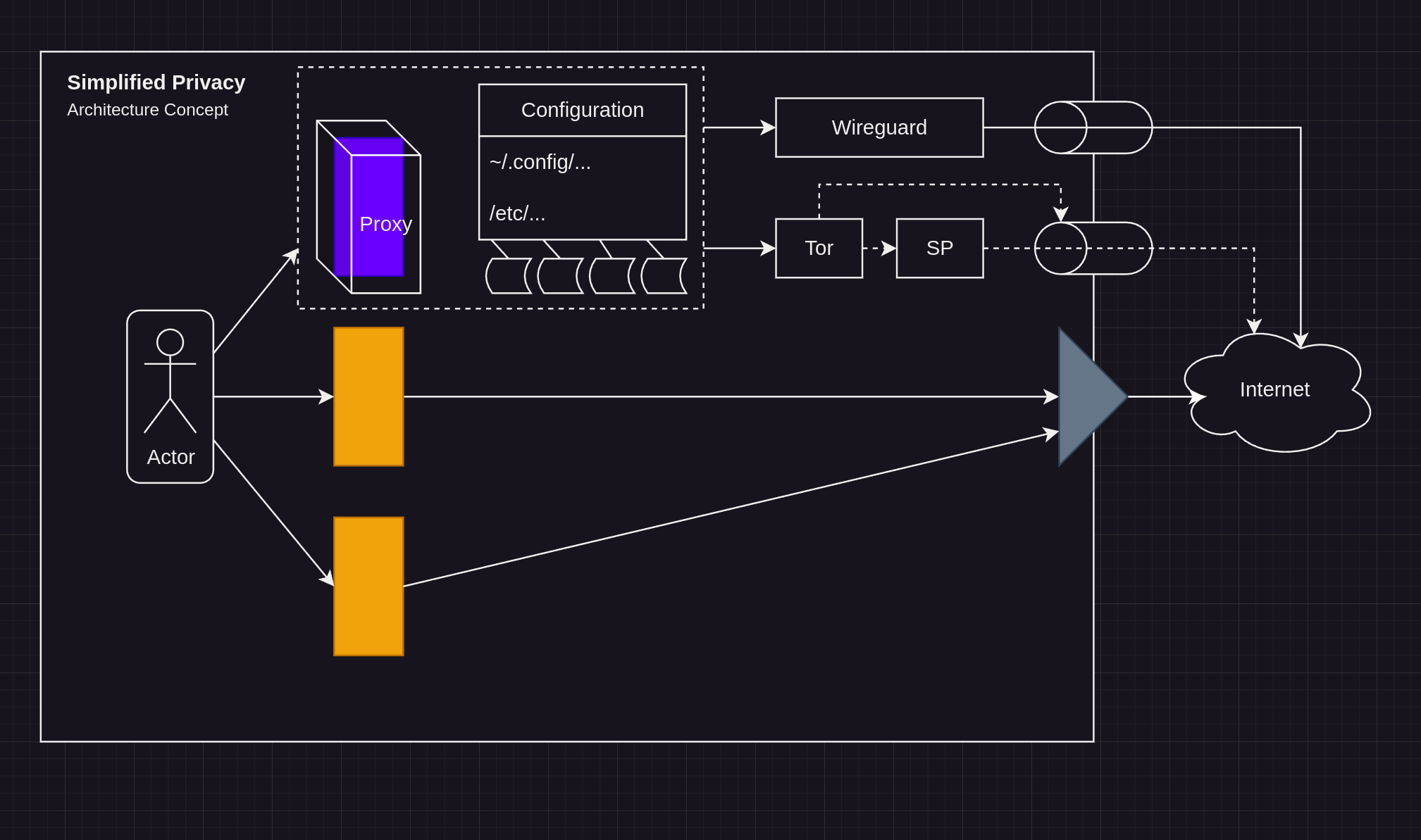
¶ How do the 2 Layers work?
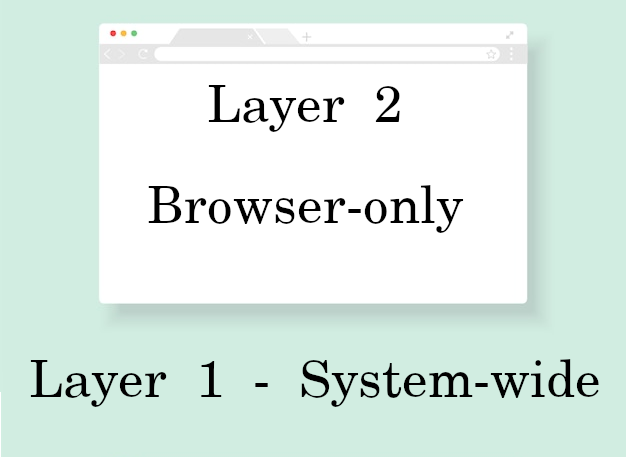
¶ System-wide (Layer 1)
You can optionally also get a system-wide connection first through us, or use a third-party provider, such as IVPN or Mullvad.
¶ Profiles (Layer 2)
The Simplified Privacy Linux client allows you to create browser-only VPN profiles. The profiles are browser-only WireGuard or Proxies.
¶ 2 Hops:
So you're doing 2 hops:
First layer is system-wide.
Second layer is the profile, browser-only.
¶ I have a slow internet connection. I don't want to do 2-hops. What can I do?
First, you should do WireGuard system-wide with a location near you. The closer to you the better.
Then for the layer 2, do a proxy because it has no encryption. It's the encryption that slows VPNs down.
If this is still too slow for your situation, you can just use system-wide WireGuard like a regular VPN. Then we're super cheap.
¶ What is the difference between WireGuard and Proxies?
¶ WireGuard
WireGuard is encrypting and hiding what websites you're visiting.
¶ Proxy
While, Socks5 Proxies just forward the traffic WITHOUT encryption. This is good for hiding Tor because you don't want even more encryption slowing Tor users down. So if you select Tor first, then a socks5 proxy, this hides from the website that you're using Tor.
¶ Tor -> Proxy
The Tor exit can still see WHICH websites are visited, but can't see the actual data because of SSL. SSL (httpS encryption) is on all websites, even without VPNs.
¶ Is HydraVeil open source?
¶ Code
Our code is published under GNU/GPLv4, with forced copy-left protection,
https://git.simplifiedprivacy.is/explore/repos
¶ Art
However, our art, logo, and artistic designs are copyright.
¶ Can I run HydraVeil from the open source code?
Yes, the client can be run and works perfectly fine directly from the Python code. However, all the required dependencies must be manually setup and installed. We have a guide on this:
Split it up from the Appimage
Direct source code
¶ Is Simplified Privacy's art public domain?
No, our HydraVeil and website art, logo, and GUI designs are published under full copyright protection to prevent malicious impersonation of our service. If a malicious actor creates a similar website and gets SEO claiming to be us, it's a security risk.
¶ Organization
¶ Who funds Simplified Privacy?
We have zero external funding, it's owned by our staff. Please consider donating or using our other services such as buying a phone or VPS combo setup with email.
¶ Where is Simplified Privacy located?
As a purely digital company, we don't have a physical brick-and-mortar legal headquarters. Instead, we're promoting a circular cryptocurrency based economy, operating under a parallel legal system with XMRBazaar. We value agora economics and alternative legal system outside of traditional financial institutions, to foster individual liberty. Under this system, we use PGP verification for identification of the business. You can find more about this arbitration system and the protections it offers you as a customer here: https://simplifiedprivacy.com/how-pgp-insurance/2025.html
Further, we live on social networks that transcend physical locations, through the use of redundant Encryption as Identity:
Website: [Arweave]
Twitter: [Nostr]
Political Facebook: [Bastyon]
Email List: [Session messenger]
¶ Audits
¶ Is there an External Security Audit?
¶ Layer 1
For our original app HydraVeil, which is fully open source, we don't yet have an external security audit. However, keep in mind that it's two layers and the system-wide layer 1 is essentially a commodity. We are doing the exact same thing as our competitors such as Mullvad and IVPN with the layer 1, which is running a linux command "wg-quick".
¶ Layer 2
For the layer-2, it's a custom environment designed to itself act as a kill switch, where it can't get the internet unless it flows through the proxy (encrypted with Wireguard, or not with socks5). Please see: https://simplifiedprivacy.com/wireguard-without-sudo-as-a-proxy/wireproxy.html
As far as speculation that our layer 2 Hydraveil is leaking due to failure on our engineering team, I don't see how the answer to this concern is to not use layer-2 at all. Because then you'd just be using the layer-1 exactly like other VPNs. And the layer-2 can be tested with DNS leaks tests.
¶ Propaganda
For an audit of our servers, this is ironic propaganda. As the external security check has no way to verify if we log. And by setting up a government registered company to do these kinds of verifications, it exposes the organization to tyrannical governments such as Switzerland now cracking down on Proton. Or Sweden cracking down on Signal. In other words, the very thing you're asking "guaranteed security" for can't be achieved, by ironically gives one the very opposite.. of opening it up to politicians to decide your fate and give gag orders. Instead, if we just use cryptocurrency among ourselves, who cares what politicians think.
¶ Solutions
Because nobody can verify if someone else's server is logging, this is why you'd want to have multiple layers like HydraVeil gives you. Until we decentralize, you could use an external provider for the layer-1, and Simplified Privacy for the layer-2 to be anonymous. We also offer Tor->socks5 proxies now. Another option is you can also put our WG config on a router, to be anonymous to a different provider. And at a $1 price point, this is realistic and easy.